In our previous article, we outlined the requirements listed in the NIS 2 Directive and their impact on companies. Today we’re going to dive into a critical aspect of NIS 2: the Vulnerability Disclosure Policy (VDP).
What is a VDP? A Vulnerability Disclosure Policy (VDP) is an official document and structured process that details how a company receives, evaluates, and manages vulnerability reports from external cybersecurity experts. This process is vital to maintaining the security of your company’s digital infrastructure. In the industry, VDPs are also known as Coordinated Vulnerability Statements (CVDs) and Responsible Disclosure Programs (RDPs). These terms are often used interchangeably to refer to the same concept of managing and managing security vulnerabilities reported by third parties.
The NIS 2 Directive requires the implementation of the VDP, depending on the implementation of the Member State. Some companies may question whether providing an email address is sufficient to report a vulnerability.
In today’s increasingly digital landscape, a well-structured Vulnerability Disclosure Policy (VDP) is more than just a good practice—it’s a necessity for any organization committed to cybersecurity. A VDP establishes a clear framework for how companies receive, assess, and address vulnerability reports from external cybersecurity professionals. This structured approach not only ensures that potential security flaws are identified and mitigated efficiently, but it also strengthens the company’s overall security posture by proactively managing risks before they can be exploited.
Beyond enhancing security, a VDP plays a crucial role in legal compliance. Many regulations, including the NIS 2 directive, require organizations to implement such policies to meet their obligations. By adhering to these legal frameworks, companies can avoid potential penalties and demonstrate their commitment to protecting sensitive data.
Moreover, a well-executed VDP can significantly boost a company’s reputation. It signals to customers,partners, and the broader public that the organization takes security seriously and is transparent in its efforts to safeguard information. This transparency fosters trust and can be a key differentiator in a competitive market.
Another critical aspect of a VDP is its role in fostering collaboration with the cybersecurity community. By encouraging third-party experts to responsibly report vulnerabilities, companies can tap into a vast pool of knowledge and expertise, further strengthening their defenses. This collaborative effort not only helps in identifying potential threats but also builds a positive relationship with the security community, which can be invaluable in the ongoing battle against cyber threats.
In summary, a well-designed VDP is essential for any organization looking to enhance its security, comply with legal requirements, manage its reputation, and foster valuable relationships within the cybersecurity community.
In this post, we’ll explain why just providing an email address isn’t enough, what the risks are with this approach, and why every company involved needs a comprehensive VDP program.
Is VDP essential part of the NIS 2 Directive?
To ensure a company can promptly identify and manage security vulnerabilities, having an official reporting channel is essential. A well-developed VDP helps companies quickly recognize security gaps in their systems and fix them before cybercriminals can exploit them.
Thus, VDP is not just a mandatory element of NIS 2 (depending on the implementation of the Member State) but a proactive tool to strengthen a company’s cybersecurity posture and reduce cybersecurity risks.
Why an email address alone isn’t enough
Last year, we carried out an extensive survey on Vulnerability Disclosure Programs (VDPs) and discovered a surprising trend: a staggering 80% of the reports submitted were classified as spam. This high volume of irrelevant submissions not only clutters the reporting process but also places a significant burden on our security teams. They are forced to invest considerable time and resources in sifting through these spam reports, validating each one to ensure that genuine vulnerabilities are not overlooked.
The influx of spam reports highlights a key challenge in managing VDPs effectively. As organizations strive to maintain robust security, the need for more efficient filtering and validation mechanisms becomes increasingly apparent. By refining these processes, companies can reduce the strain on their teams and focus on addressing real security threats more swiftly.
Moreover, addressing the issue of spam within VDPs is essential for maintaining the effectiveness of the program. Without proper management, the overwhelming volume of spam can dilute the value of the reports and potentially lead to critical vulnerabilities being missed. Therefore, it is crucial for organizations to implement advanced tools and strategies to filter out spam and streamline the vulnerability reporting process.
In summary, while VDPs are vital for identifying and mitigating security risks, the challenge of managing spam reports underscores the need for continuous improvement in how these programs are administered. By enhancing the efficiency of report validation, organizations can better protect themselves against genuine threats and maintain the effectiveness of their VDPs.
Choosing a Managed VDP has several key benefits. It provides legal protection for ethical hackers and creates a clear channel for them to report vulnerabilities. This method is expected to increase the number of reported vulnerabilities, ensuring they are quickly communicated and addressed. By using a managed VDP, we can make the validation process more efficient, improve our security measures, and create a legally compliant environment for reporting vulnerabilities.
Lack of structure:The use of an email address for handling vulnerability reports often results in a lack of structured processes, leading to potential mismanagement. One major issue is the ambiguity surrounding who is responsible for reviewing the reports, which can cause significant delays and inefficiencies. Additionally, without a defined process, the response time to hackers regarding reported issues can vary greatly, leading to frustration and potential security risks. Addressing these concerns by implementing a clear and structured vulnerability disclosure process can ensure more efficient management and timely responses, ultimately enhancing the overall security posture of the organization.
Security risks: Without a formal VDP, sensitive information might be mishandled, increasing the risk of data breaches.
Compliance issues: Simply providing an email address may not meet the compliance requirements set by the NIS 2 Directive, ISO/IEC 29147: Vulnerability disclosure and ISO/IEC 30111: Vulnerability handling processes.
Importance of a well-designed VDP
Enhanced security: A structured VDP ensures that vulnerabilities are identified and addressed promptly, reducing the risk of exploitation.
Trust building: Demonstrating a commitment to security through a VDP builds trust with customers and stakeholders.
Regulatory compliance: A comprehensive VDP helps companies comply with legal and regulatory requirements, avoiding potential fines and penalties.
Implementing a robust VDP is not just about compliance; it is a critical component of a company’s overall cybersecurity strategy. By proactively managing vulnerabilities, companies can protect their assets, reputation, and customers. The NIS2 directive has underscored the importance of efficient vulnerability management. For cybersecurity experts and company leaders, a managed Vulnerability Disclosure Program (mVDP) offers numerous advantages over traditional VDPs.
Consequences of neglecting Vulnerability Disclosure Policy
Neglecting a Vulnerability Disclosure Policy (VDP) can expose an organization to significant risks, undermining its security and reputation. Without an official channel for ethical hackers to report security vulnerabilities, the discovery of these issues can be delayed, posing serious risks to system security. Hidden vulnerabilities become prime targets for cybercriminals, increasing the likelihood of exploitation.
The absence of a VDP also brings substantial legal and reputational risks. If a vulnerability leads to data loss or other damages. Beyond legal consequences, public perception can suffer, especially if incidents are not handled transparently. The greatest loss, however, is the erosion of trust, as customers and partners may no longer believe in the company’s ability to protect valuable data.
Furthermore, without well-structured processes for handling security reports, teams can become overwhelmed with unchecked or irrelevant information. An overburdened IT team cannot effectively manage the influx of information, leading to wasted time and resources. Consequently, critical vulnerability information from external sources may get lost in the noise, creating security blind spots.
Compliance issues are another critical concern. The absence of a VDP poses serious legal and business risks. Companies that fail to comply with cybersecurity regulations may face severe financial penalties, further damaging their financial standing and market reputation.
Overall, a company without a VDP is more likely to become a target for cyberattacks, leading to legal problems and reputational damage. The lack of a VDP also hinders the company’s ability to build a robust security system and foster collaborative relationships with the cybersecurity community. By implementing a comprehensive VDP, organizations can mitigate these risks, ensuring a more secure and trustworthy environment for their stakeholders.
How to set up your managed VDP?
Framework development: We help define the VDP content to ensure legal protection for those who report vulnerabilities in the prescribed manner.
Using Hackrate vulnerability reporting form: Our team assists in embedding the vulnerability reporting form on the company’s website. It is important to clearly indicate that active security testing is not encouraged.
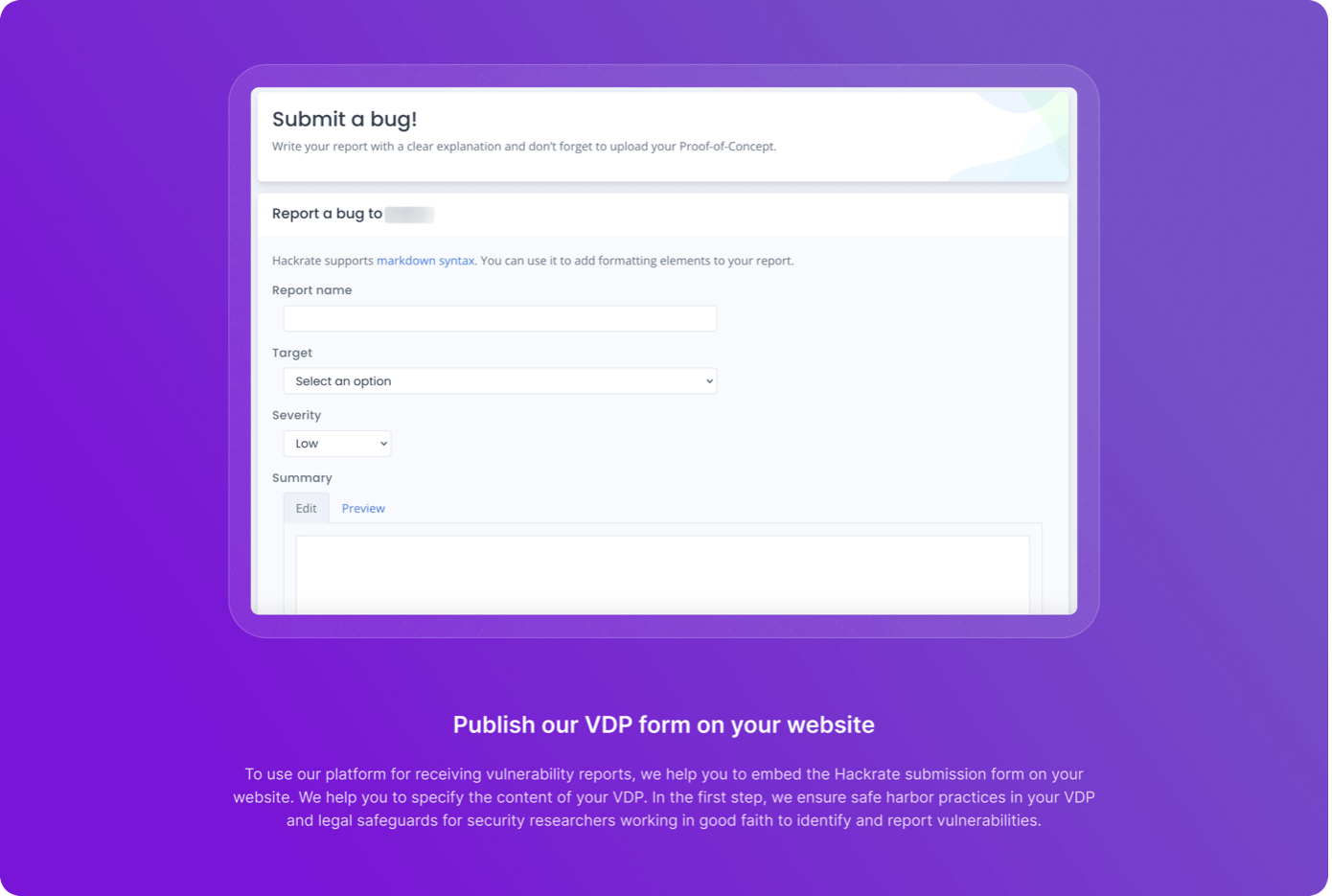
- Receiving validated reports: We validate all incoming reports through the platform before forwarding them to the company’s IT team.
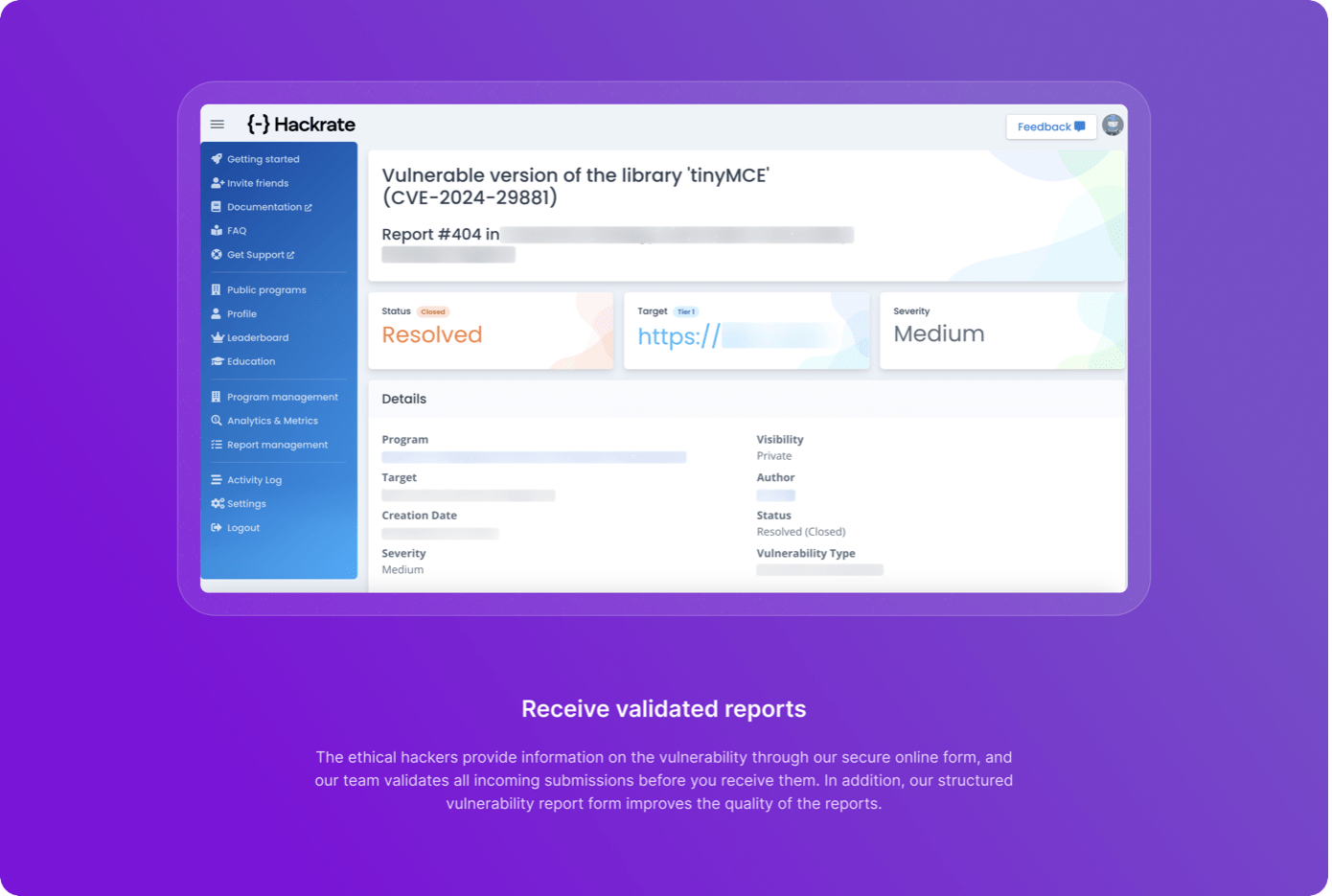
- Managing vulnerabilities: The final step involves managing and fixing the reported vulnerabilities. Throughout the process, the Hackrate team facilitates communication between the company and ethical hackers.
Partner with Hackrate for VDP implementation
Partnering with us for the implementation of a Vulnerability Disclosure Program (VDP) is a strategic move that can significantly enhance your organization’s cybersecurity posture. Implementing and operating a VDP is a complex task fraught with numerous challenges, but collaborating with an experienced cybersecurity firm like Hackrate offers several key advantages.
Firstly, Hackrate brings expert knowledge and extensive experience to the table. Our team, well-versed in VDPs, possesses the necessary expertise to create and maintain an effective and reliable framework over the long term. This ensures that your VDP is not only robust but also adaptable to evolving security threats.
Continuous monitoring is another critical aspect. Monitoring and managing incoming reports can be time-consuming and overwhelming for internal teams. Hackrate’s expert team ensures that every report receives the necessary attention, allowing your company to respond promptly and efficiently to potential vulnerabilities.
Technical expertise is crucial for handling VDP-related tasks, which often require deep technical knowledge. Our experienced team can manage complex technical issues and find appropriate solutions, ensuring that vulnerabilities are addressed effectively and efficiently.
Process optimization is another area where Hackrate can make a significant impact. Our team can help streamline the processes for handling reports, reducing the number of false positives and increasing the program’s overall efficiency. This optimization not only saves time and resources but also ensures that critical vulnerabilities are not overlooked.
Moreover, Hackrate can develop a structured reporting interface that simplifies report management and filters out false positives. This structured approach ensures that your IT team can focus on genuine threats, enhancing the overall effectiveness of your VDP.
In summary, partnering with Hackrate for VDP implementation offers numerous benefits, including expert knowledge, continuous monitoring, technical expertise, process optimization, legal compliance, and a structured reporting interface. This collaboration enables your company to manage security risks more effectively, protect valuable data, and foster a safer environment for your stakeholders. By leveraging Hackrate’s expertise, you can build a robust security system.
How can we help?
The Hackrate team boasts years of experience in the field of Vulnerability Disclosure Programs, with numerous international references. Our managed VDP program enables you to effectively identify and address your company’s vulnerabilities, significantly reducing cybersecurity risks.
For detailed information about our VDP services, visit: Managed Vulnerability Disclosure.
For inquiries about VDP and cybersecurity solutions, reach out to us here or via email (sales@hckrt.com).

